By Ashith Bolar , Partner and Director AmBr Data Labs
Lack of user-acceptance is considered a failure of any new Information System — a rule that equally applies to a Business Intelligence initiative. And the astounding fact is that this is a very common occurrence. The reasons can be varied, such as the quality of data, the usefulness of the analytics provided by the system, or merely the user-interface being unfriendly.
However, what is not considered in assessing the success or failure of the system is the number of users who did not get access the system — an error of omission (pun intended). Typical IT projects finalize the initial set of end-users right at the inception of the project, and no later than the requirements phase. To manage the scope of the project, it is typical to keep a small and manageable initial user-base. However, I believe that this is a mistake!
I believe it is a mistake, that in trying to ensure the success of the project, the scope of the BI deployment should be restricted to a few. The true value of a BI enterprise is the crowd-sourced intelligence that you derive from it — and by this assertion: the more the merrier! Not only will a wider audience give us a better assessment of the success of our BI initiative, it will also ensure wider and quicker post-deployment enhancements.
Starting with a large audience of users has many challenges, least of which is managing the scope of the BI project. Given that a data warehouse typically contains sensitive data, one of the main concerns of a large user-base is data security — ensuring that only the right users get access to the right data. This concern leads to the usual decision of limiting the initial user-base to just the power-users, ones that require none or minimal data security.
We see your challenge and raise you AccessOne©!
AccessOne is an information security software specifically designed for SAP™ Business Warehouse (SAP-BW). AccessOne allows you to build your access-control security in an easy excel-like matrix, and deploy it with a few clicks. AccessOne can extract access information from your ECC system (be it role-based, structural authorizations, etc) or a traditional SoD ACL matrix, or even an excel file you created on your desktop.
So that you can visualize AccessOne more completely–
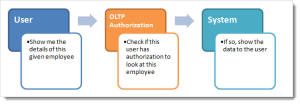
A BI solution’s data security implementation is quite different from an OLTP system, even though they both try to achieve the same goal by means of a same set of parameters. The OLAP authorization mechanism works in the reverse direction of the procedures employed by an OLTP system.
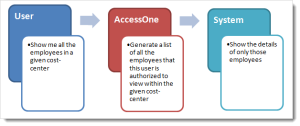
See schematic below:
Take an example of an OLTP HR system / employee database. Here’s the sequence of events that occur when a user interacts with the system:
Now consider its BI counterpart. The typical user request sequence goes something like this:
Although, this is a simplified view, it’s easy to visualize the change in the mechanics of how authorization works between an OLTP and an OLAP system.
The power of AccessOne is in its ability to transform security parameters from the data structures that are designed for an OLTP system to the ones that are more suitable for an OLAP system. Moreover, AccessOne applies these authorization checks to any and all users of the SAP BI system. It will replicate your OLTP (ECC) system access parameters (role-based, structural, etc) into OLAP (SAP BW) system access parameters (analysis authorization).
With this power, and with the guarantee that your BI system access is exactly the same as your ECC, you can now open up your BI system to all the ECC system users, be it power users, domain-specific users, supervisors, or individual-contributors.
Another power of AccessOne is “overriding” or “overloading” authorizations derived from OLTP. With a single access-control entry, you can override or overload (add to) the access of any user or user-group. For instance, if you have an end-user with limited access in the Finance ECC system, however you want to provide this user with extended access to the BW system on the finance cubes, this can be achieved by inserting a single access-control entry in the BI system.
In the following blog posts, we will examine some complicated yet typical case-studies to illustrate the power of AccessOne.
– Watch this Space –



Leave A Comment